[Guide] Linux Remote Access Behind Firewall: Easy Steps!
Are you struggling to access your Linux servers remotely, only to be thwarted by the ubiquitous firewall? Mastering the art of Linux remote access behind a firewall is not just a technical skill; it's a gateway to efficient system administration, secure data access, and unparalleled control over your digital infrastructure. But how do you navigate the complex labyrinth of network security while maintaining seamless connectivity?
The challenge of establishing remote access to a Linux server residing behind a firewall is a common one, faced by system administrators, developers, and IT professionals worldwide. Firewalls, the vigilant sentinels of network security, are designed to protect systems from unauthorized access. They meticulously scrutinize incoming and outgoing network traffic, blocking any communication that doesn't conform to pre-defined rules. While essential for safeguarding sensitive data and preventing malicious attacks, firewalls can also inadvertently obstruct legitimate remote access attempts. This creates a frustrating paradox: the very security measures designed to protect your system can also make it nearly impossible to manage it remotely.
The key to overcoming this hurdle lies in a multifaceted approach, one that blends technical prowess with a solid understanding of network fundamentals and security best practices. It involves strategically configuring the firewall to permit authorized connections, utilizing secure protocols for data transmission, and implementing robust authentication mechanisms to verify user identities. Furthermore, the specific method employed will often depend on the particular firewall in use, the network topology, and the level of security required. This article will delve into several practical techniques and tools for establishing secure Linux remote access behind firewalls, exploring the nuances of each approach and providing clear, concise guidance to empower you to take control of your remote access needs.
Let's begin by examining some of the most prevalent methods used to achieve secure remote access. One of the most fundamental approaches is port forwarding. Port forwarding involves configuring the firewall to forward incoming traffic on a specific port to a specific internal server. This allows external connections to reach the Linux server through the firewall. SSH (Secure Shell) is the standard protocol for secure remote access to Linux servers, providing an encrypted channel for command-line access and file transfer. When used with port forwarding, SSH allows you to securely connect to your server from anywhere on the internet.
Another critical aspect to consider is the concept of a VPN (Virtual Private Network). A VPN creates an encrypted tunnel between your remote device and the server's network, effectively bypassing the firewall's restrictions. This allows you to access the server as if you were directly connected to the local network. VPNs are particularly useful in situations where multiple devices need remote access or when more robust security is needed. When setting up a VPN, you should carefully choose the VPN protocol and the encryption methods to ensure the highest possible level of security. There are several open-source VPN solutions, such as OpenVPN, that are popular among system administrators because they provide flexible configuration options and strong encryption.
The use of a reverse proxy is another valuable technique in your arsenal. A reverse proxy acts as an intermediary between the client and the server, handling incoming requests and forwarding them to the appropriate server. This can provide an additional layer of security by hiding the internal structure of your network from the outside world. Reverse proxies also offer advantages such as load balancing and caching, which can improve the performance of your applications. When using a reverse proxy, it's essential to configure it properly to ensure that all traffic is encrypted and that access is restricted to authorized users.
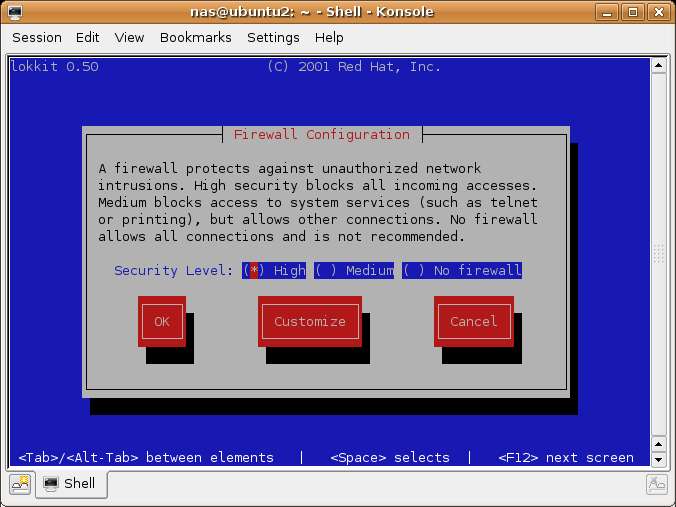
Finally, let's not forget about the importance of security best practices. Always use strong passwords, and regularly update your server's software to patch any security vulnerabilities. Enable two-factor authentication (2FA) for an extra layer of security. Regularly monitor your server's logs for any suspicious activity. Regularly review firewall rules to remove any unnecessary or outdated rules. By following these simple but very essential steps, you will significantly improve the security of your remote access setup.
To illustrate how these principles are applied in practice, consider a scenario where you have a Linux server running behind a firewall. The server is running SSH on port 22, and you want to access it remotely. Here is an example of implementing port forwarding using the `iptables` firewall rules:
First, ensure that you have `iptables` installed. If not, install it using your distribution's package manager, such as `apt-get` or `yum`. Then, to forward traffic from port 22 on the external interface to port 22 on the internal server, you might use a command like:
`sudo iptables -A PREROUTING -t nat -i eth0 -p tcp --dport 22 -j DNAT --to-destination :22`
`sudo iptables -A FORWARD -p tcp -d --dport 22 -j ACCEPT`
`sudo iptables -A INPUT -p tcp --dport 22 -j ACCEPT`
where `` is the internal IP address of your Linux server, and `eth0` is the external interface of your firewall. After setting the firewall rules, you need to enable port forwarding on the firewall. Then, you can connect to your server from any device by opening an SSH client and connecting to your firewall's public IP address on port 22.
For more advanced scenarios, implementing a VPN solution might be the preferred approach. Let's consider the implementation of OpenVPN server. OpenVPN is a well-respected open-source VPN software that enables a high degree of security and is easy to configure. To set up an OpenVPN server on your Linux machine, first, install the OpenVPN package and the related tools: `easy-rsa`. Follow the step-by-step process as per documentation and best practice. For example, to generate the necessary certificates and keys, you'll need to initialize the `easy-rsa` environment, generate a certificate authority (CA), a server certificate and key, and client certificates. After the certificate generation phase, configure the OpenVPN server by creating the server configuration file (`server.conf`). This file will contain parameters like the network interfaces, the port number, the VPN subnet, and the location of the certificates and keys.
Once the OpenVPN server is set up, you can configure the firewall to allow traffic on the VPN port (typically UDP port 1194). Similar to the port forwarding, this will involve adding rules to allow the incoming UDP traffic on the chosen port. After setting up the server and the firewall, the client needs to be configured. For each client that will be connected to the VPN, you need to have client configuration files. These will contain the VPN server's public IP or hostname, the port number, and the client certificate and key. Once everything has been configured, connect the client to the VPN server, and you are all set for remote access.
As we've seen, establishing remote access behind firewalls presents a significant challenge, but it's a challenge that can be overcome. The key lies in choosing the appropriate method based on your specific needs, coupled with a commitment to robust security practices. By implementing port forwarding, VPNs, or reverse proxies, and securing your system with strong passwords, two-factor authentication, and regular updates, you can successfully navigate the complexities of remote access and maintain control over your Linux servers. Remember, the perfect solution is not just about technical implementation; it's about a holistic approach to security, where awareness, best practices, and a proactive mindset are paramount. The combination of these measures will provide you with a secure and reliable remote access solution, empowering you to manage your Linux infrastructure with confidence, anytime, anywhere. As technology evolves, so should our approach to security, so keep abreast of new tools and techniques. With the right knowledge and a vigilant approach, you can confidently unlock the full potential of your Linux systems, regardless of the firewall's presence.
In the grand scheme of network administration, the ability to remotely access a Linux server behind a firewall is a critical skill. It's about ensuring that your digital assets are not only protected but also accessible when you need them. This demands a solid understanding of the technologies we discussed above, a willingness to adapt to the ever-changing security landscape, and a constant commitment to best practices. Your ability to establish a secure, reliable, and efficient remote access solution will be the key to your success in managing your digital infrastructure.